We’ve made some major improvements to data shown on the Surface Management page. We’ve also made a few updates to Attack Surface Custom Policies, our API keys, and Application Scanning.
Fingerprinted technologies now shown on the Surface Management page
Keeping track of what technologies are being utilized across your attack surface has become virtually impossible as a result of the pace of innovation, developer methodologies, and many other factors. Questions such as, “Where am I hosting all of my WordPress sites? Or “What 3rd-party software is it using?” often go unanswered because of the sheer number of domains organizations now have to monitor.
Today, Surface Monitoring users will now know what technologies they are hosting on their attack surface.
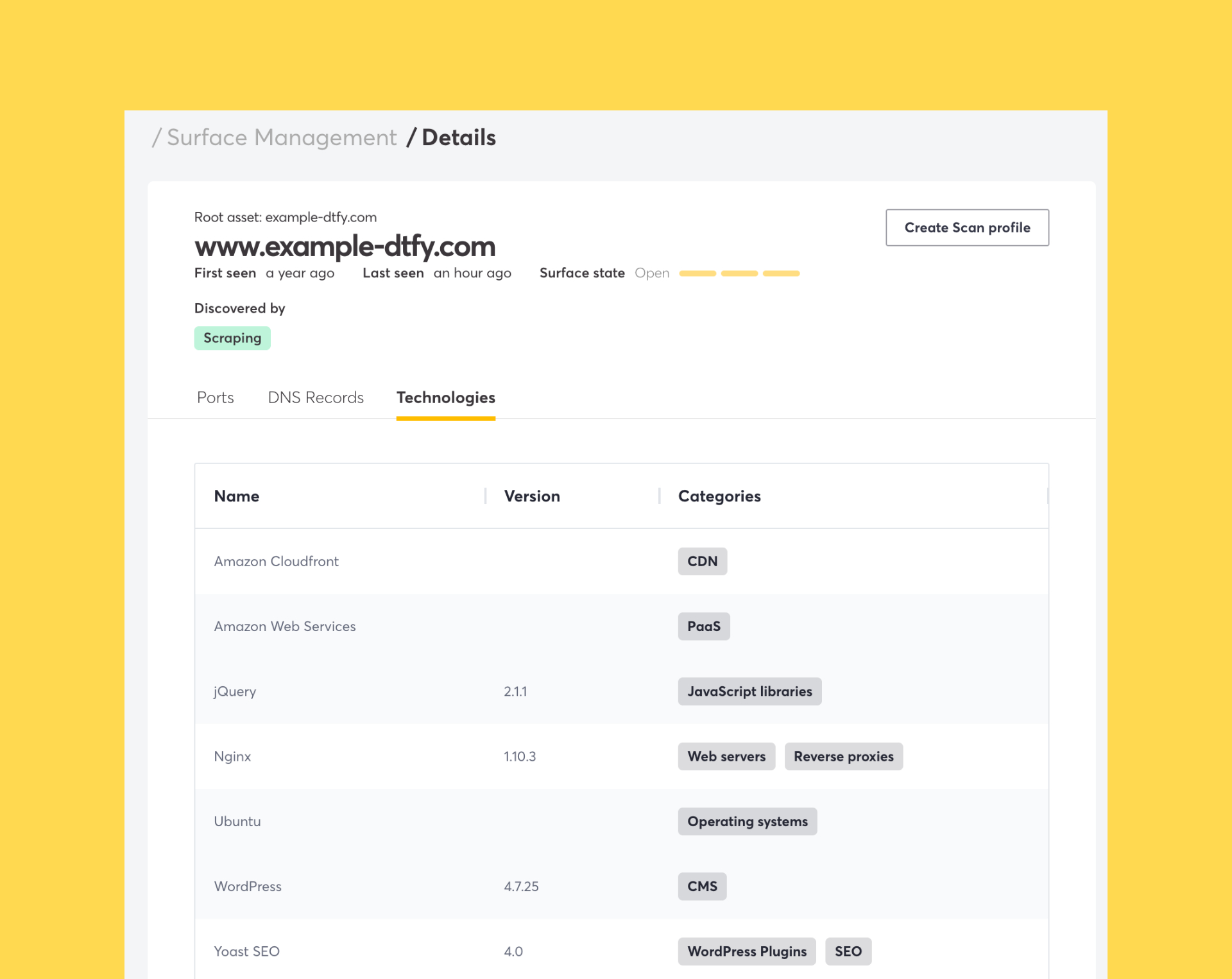
Surface Monitoring users will also be able to see technologies in different ways:
- By selecting a domain to see which technologies are hosted for a specific domain
- By selecting /Technologies from the Surface Management page for an overview of all unique technologies and versions across their entire attack surface
Users will soon be able to set Attack Surface Custom Policies on technologies on their attack surface, such as ensuring a specific technology is not used. Please keep an eye out for an update on using technologies with Attack Surface Custom Policies.
Managing API keys just got a whole lot easier
Earlier this year, we made some major updates to our API as we believe Product Security and AppSec teams should have access to the latest data about their attack surface regardless of their existing security workflows. Today, hundreds of security teams rely on our API to get critical insights in a simple, developer-friendly way.
That’s why we’re excited to announce that it’s now possible for Enterprise customers to give each API-key a name and brief description. This new functionality can be found from the /Account settings page in the platform.

If you’re not sure you have access to this feature or are interested in trying this feature, you can contact Detectify Support by logging into the platform to learn more.
Helpful reminder for Attack Surface Custom Policies
We launched Attack Surface Custom Policies in October and have subsequently helped identify thousands of potential risks across our customer’s attack surfaces. This new feature is built directly into Surface Monitoring that makes it possible to create customizable security policies across your attack surface.
We’ve now made it possible to easily view the conditions used for a specific policy, such as those AppSec teams who want to ensure that they are alerted if an open port except 80 or 443 are discovered.
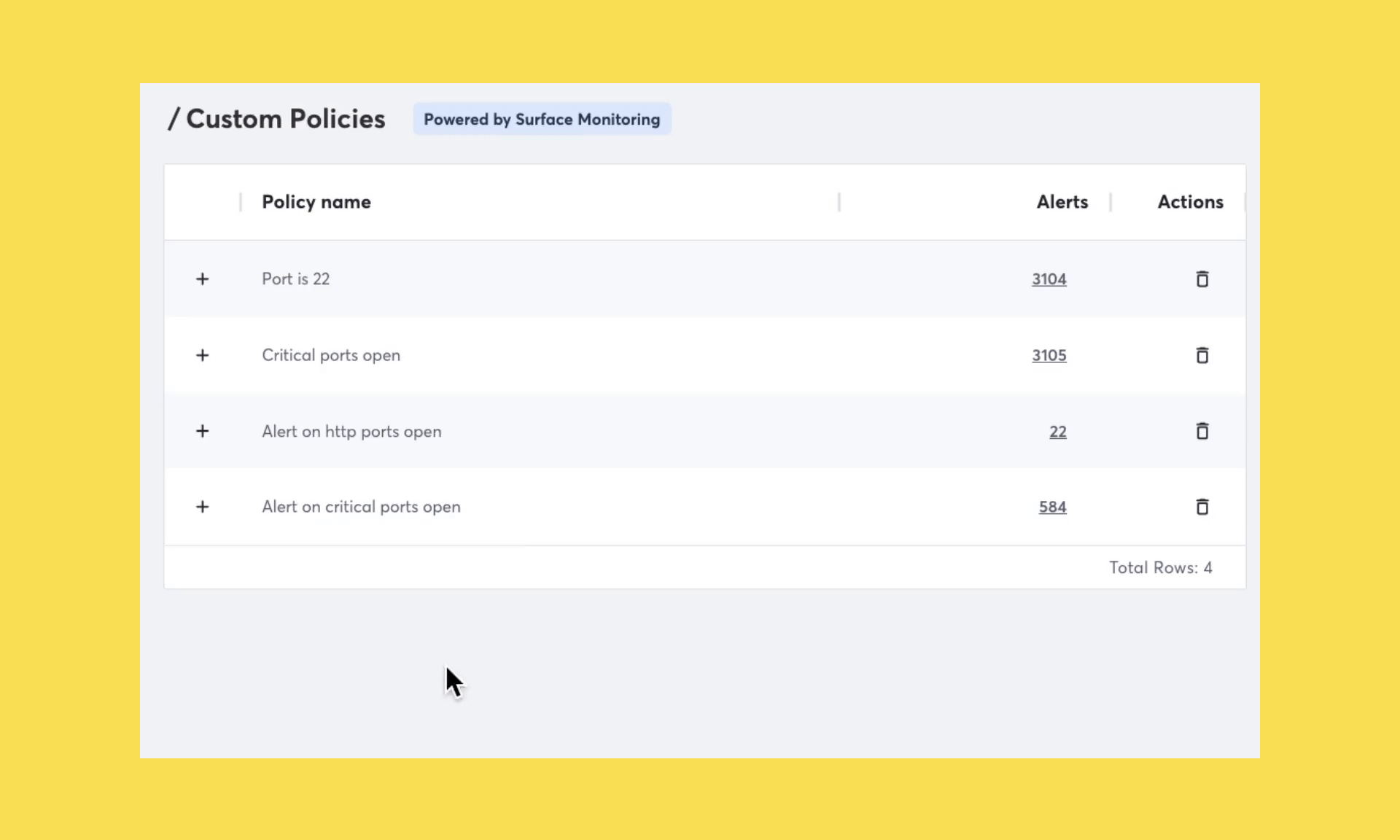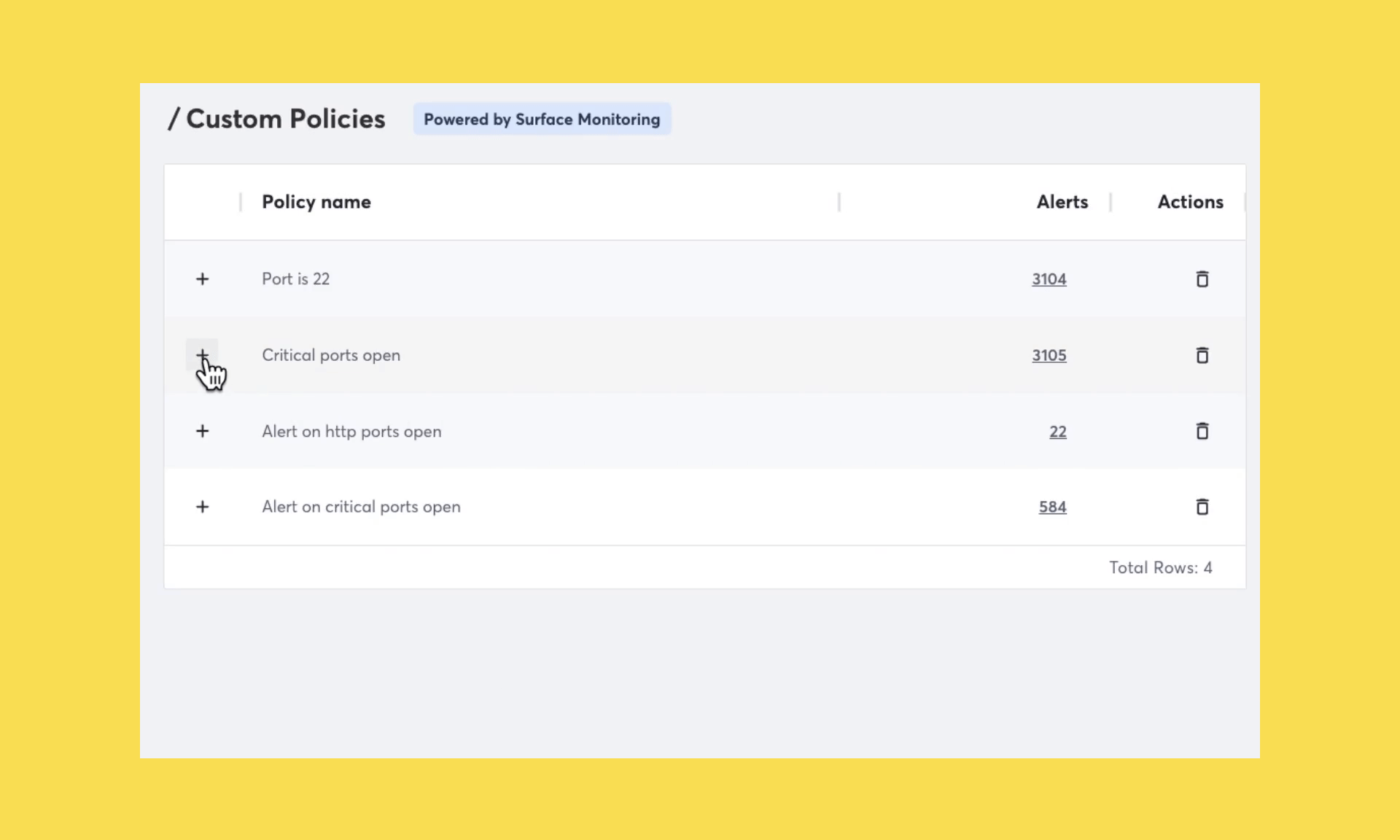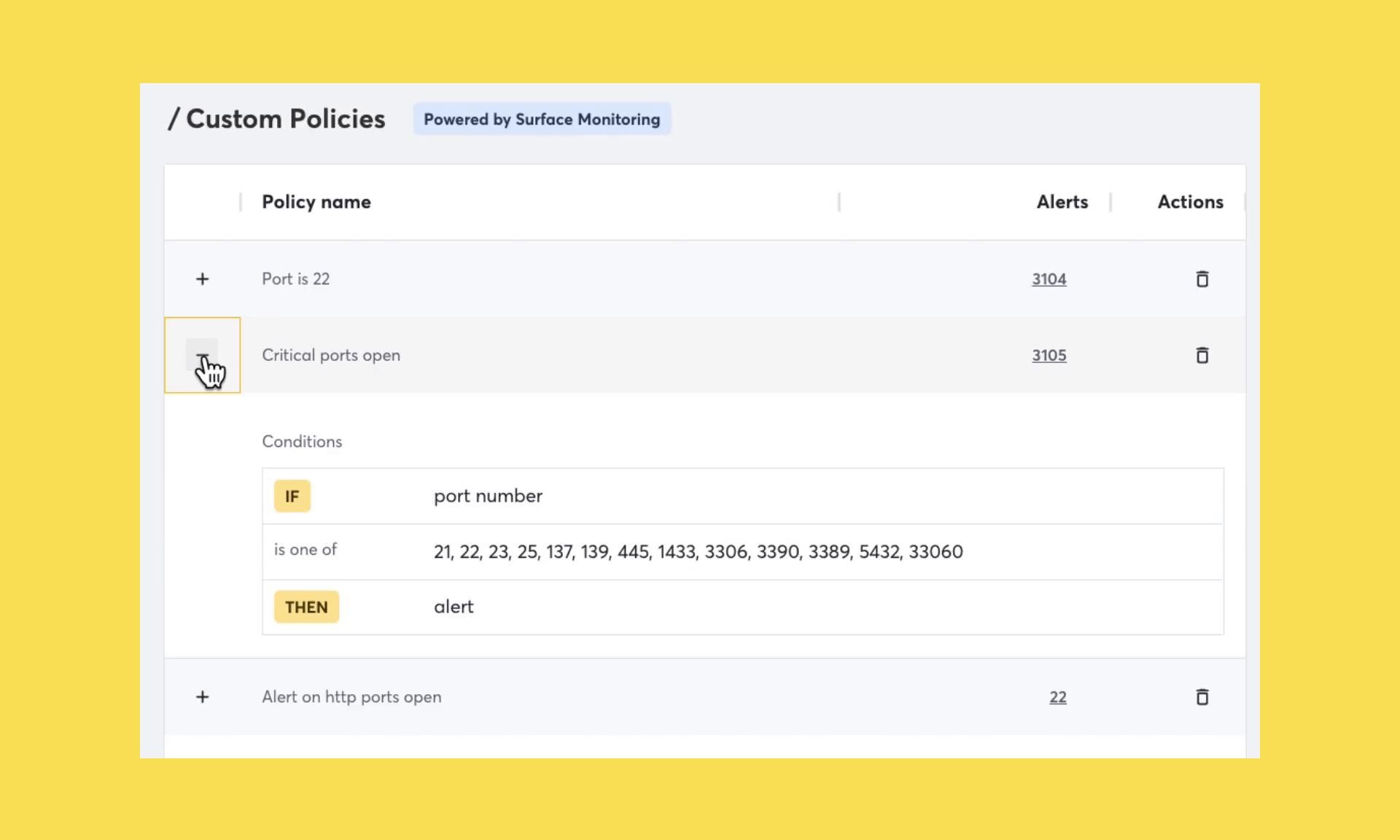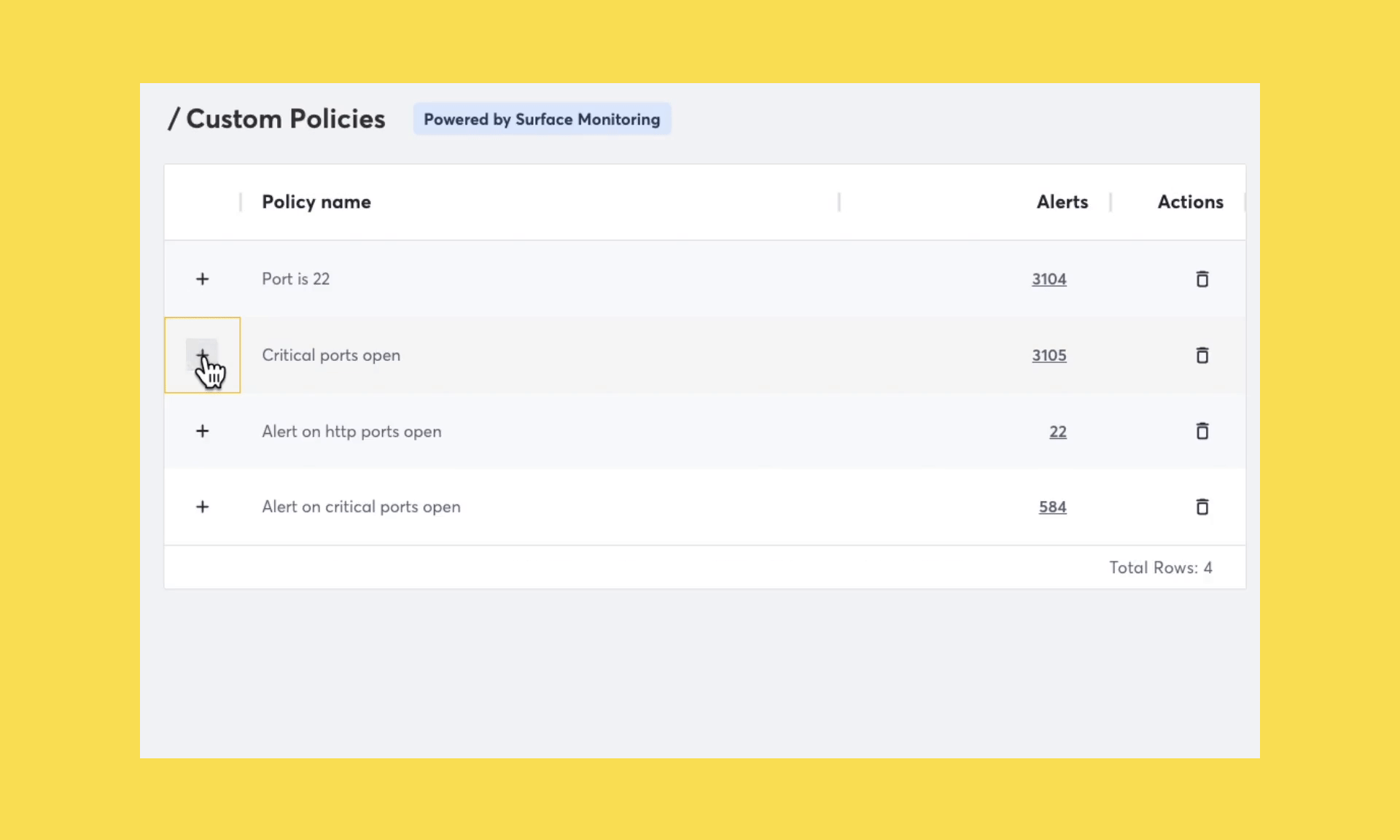
Today, security teams can use Attack Surface Custom Policies on open ports. In the coming weeks, we will begin rolling out additional functionality. Future improvements include scoping custom policies to specific domains, technologies, and much more.
Additional improvements:
- We released a new version of the Detectify Recorder Chrome Extension which is simpler to use. This new version will automatically update for existing extension users and requires no action.
- We’ve added a notification that alerts Application Scanning customers if they have experienced a failed scan. This notification can be seen via Scan Management in the main navigation bar.
Recently added crowdsourced vulnerabilities
Here is a list of all new medium, high, and critical severity modules added in the recent days from our community of ethical hackers. You can find a complete list of new vulnerabilities added to Surface Monitoring and Application Scanning by viewing the “What’s New?” section in-tool.
- Dataiku Default Credentials
- DF-Respons Local File Inclusion
If you’re interested in trying Detectify, book a demo or sign up for a 2-week free trial and start testing your web apps with Detectify today.








