We shipped a new feature called Groups which allows users to organize assets, such as domains, according to any logic that best suits the way their team works.
Meet Groups: a more intuitive way to group assets
Security teams have more data about their attack surfaces than ever before. Today, Detectify continuously monitors over 3 million domains (up from 700k around this time last year). As the attack surface grows, so does that amount of data that security teams have to manage. And security teams are feeling the pinch.
We’re excited to announce Groups, a more intuitive approach to grouping assets across your attack surface. With Groups, users can organize assets according to logic that best suits their teams. For example, you might have teams that work with vulnerability and risk findings in different ways.
Groups make it possible to organize your assets in multiple ways, for instance per technology, responsibility or priority.
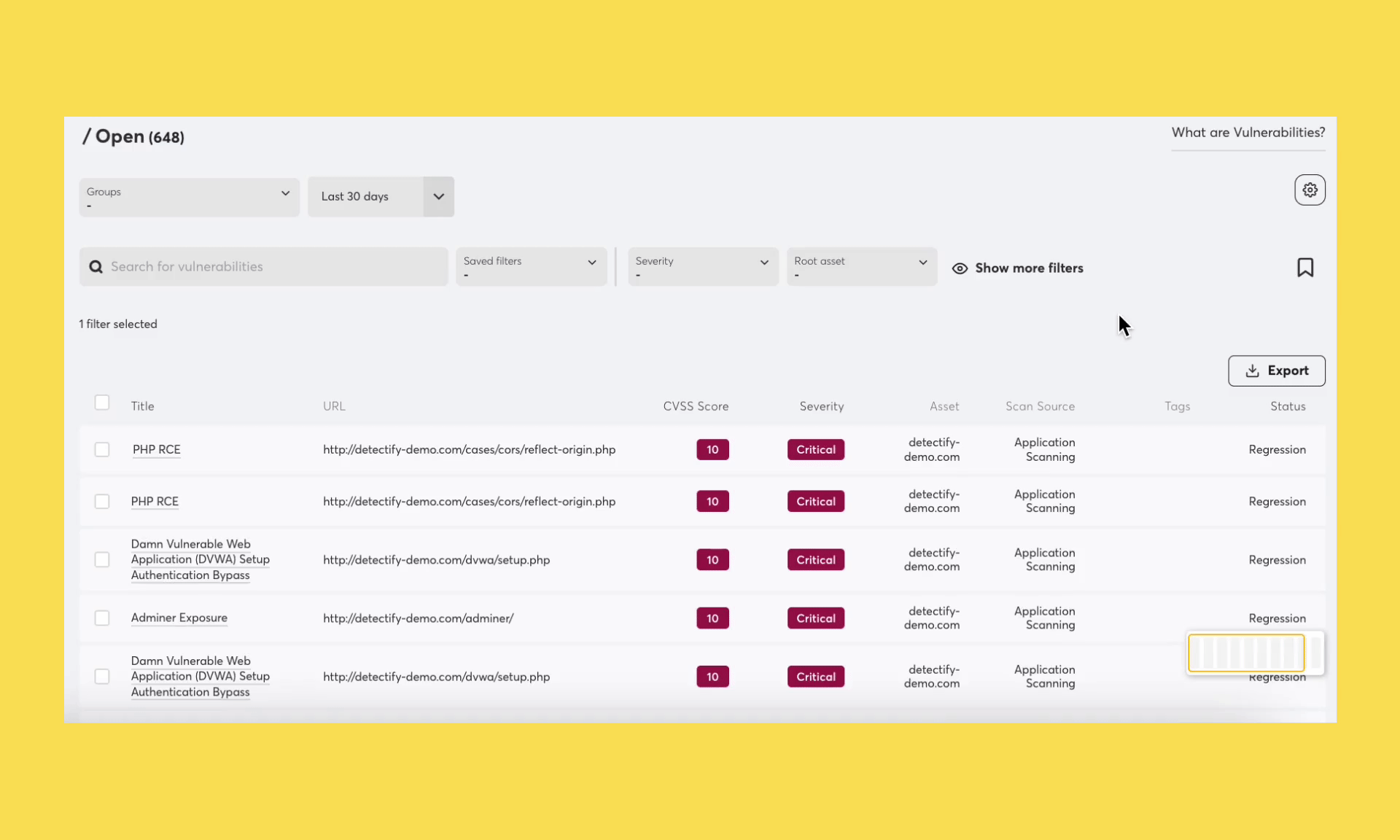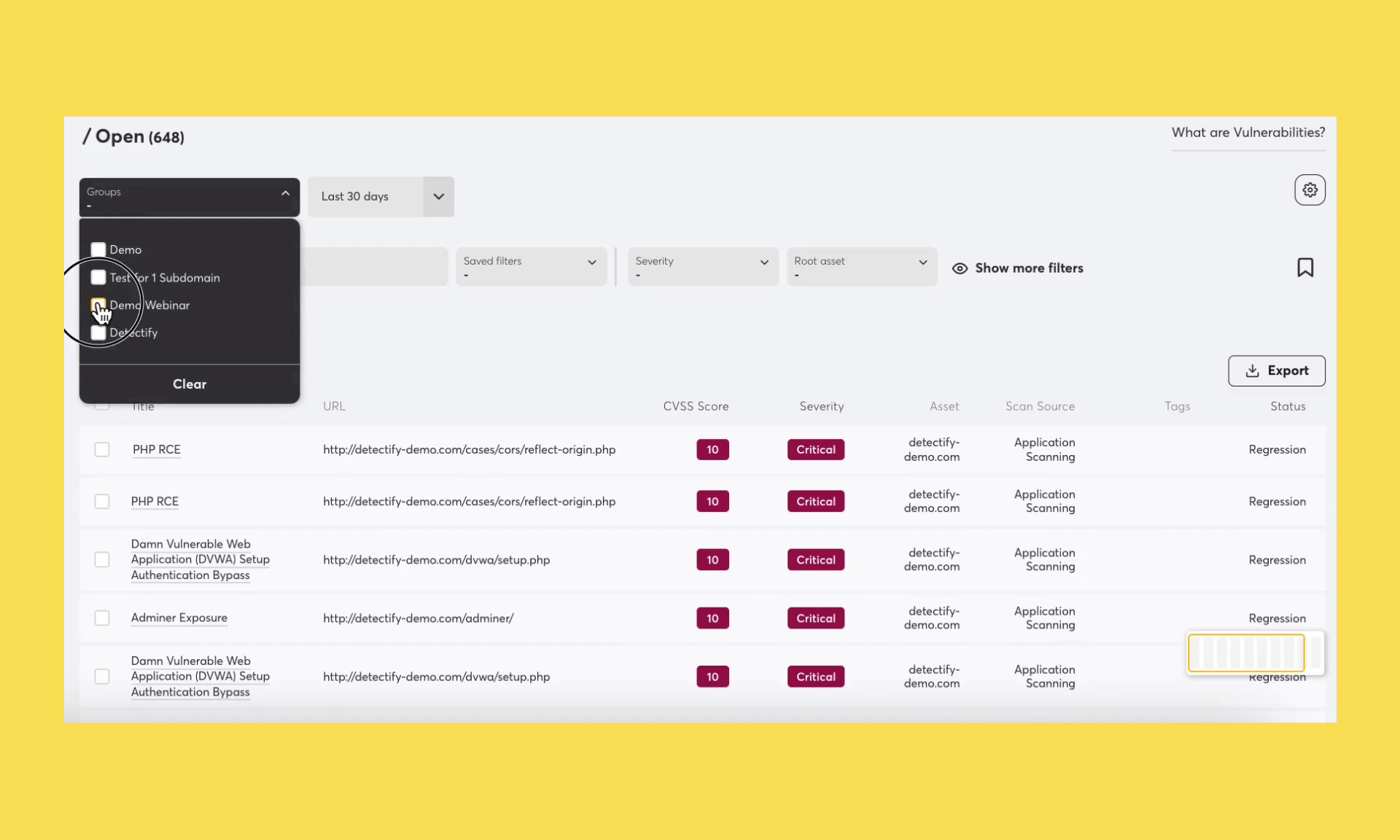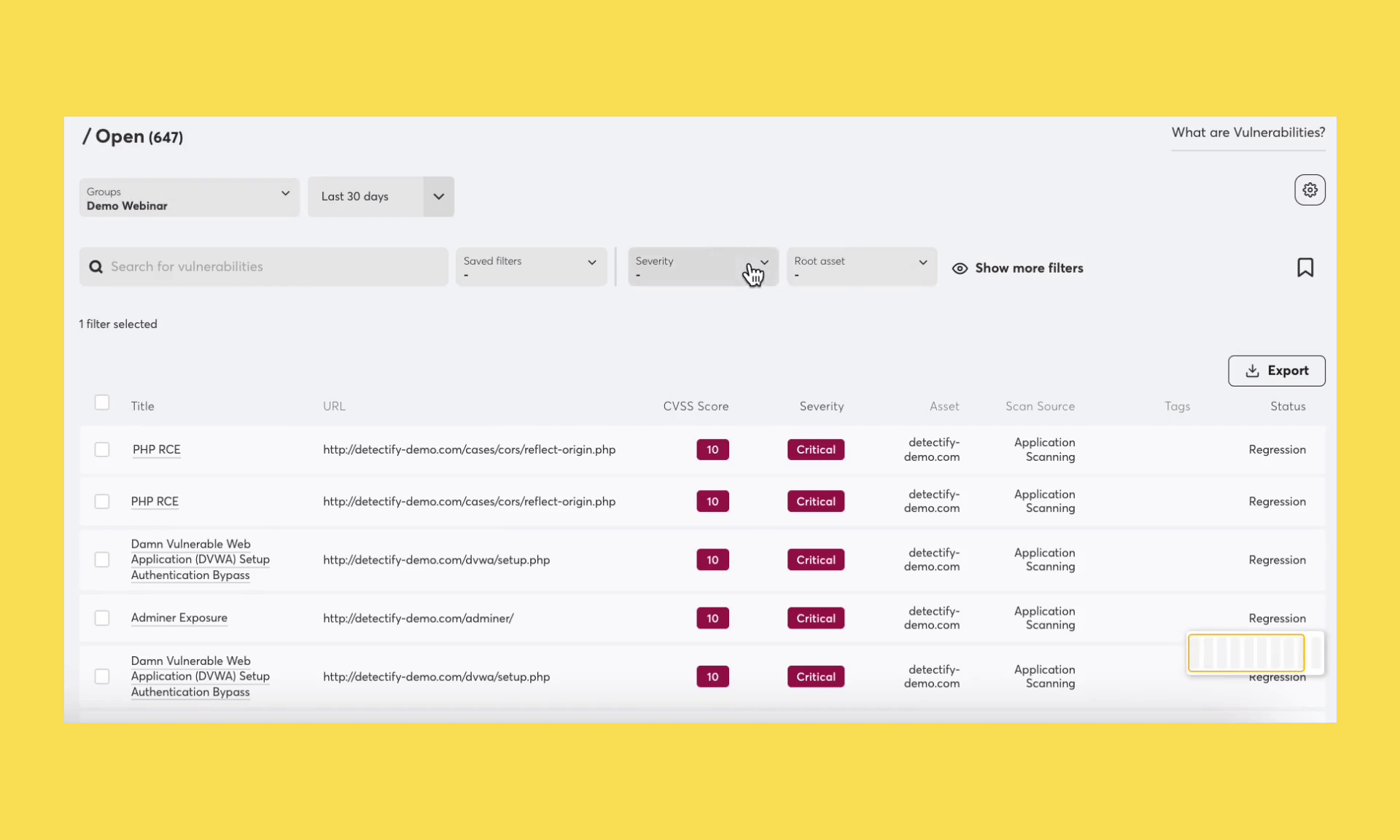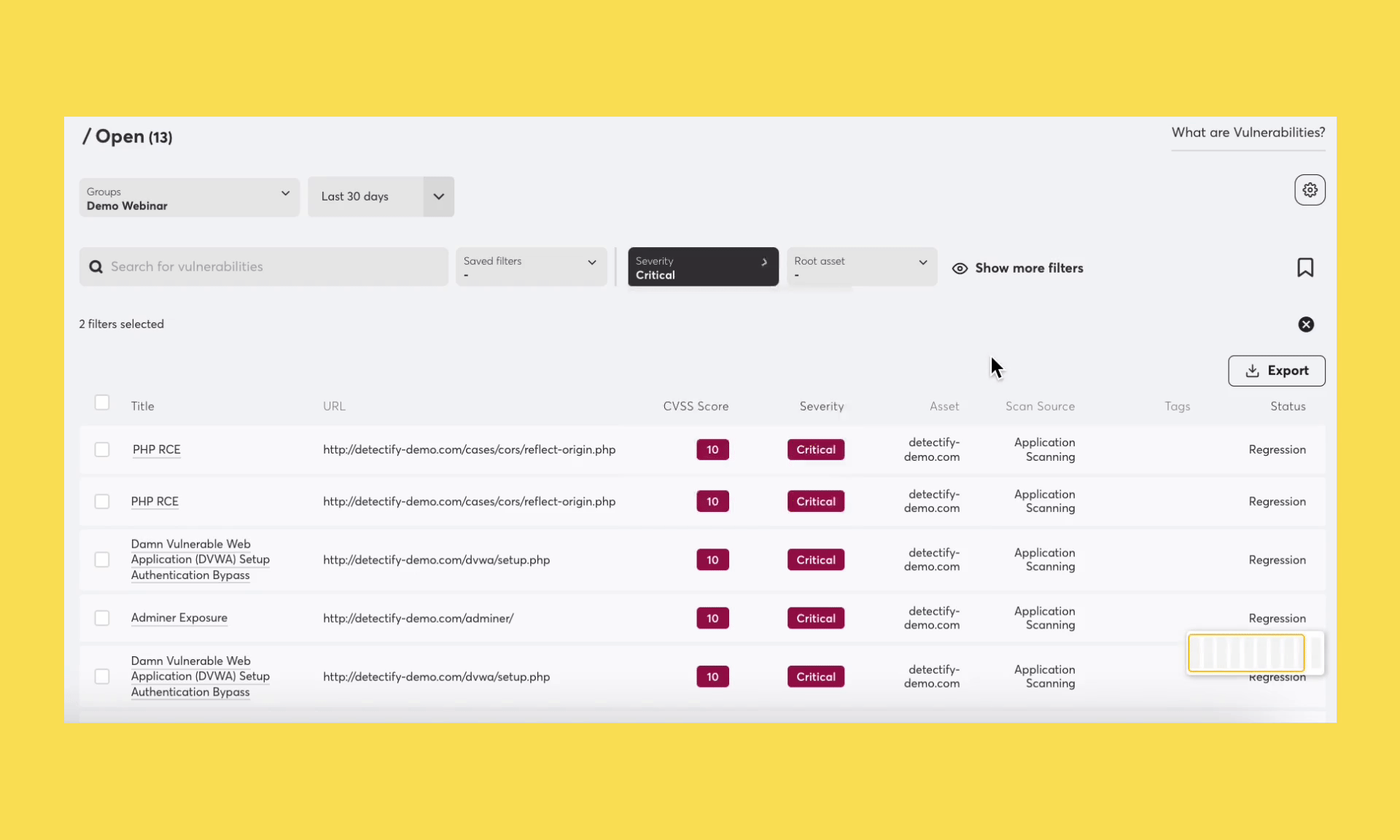
Have any questions about using groups? Get in touch with your Customer Success Manager or write to our support team.
Navigate through our tool with greater ease
We know that security teams are often managing dozens of tools to cover their expanding attack surface. With that in mind, we constantly strive to create an experience in our tool that is simple to use, regardless of how often you login. That’s why we’re excited to share that we’ve made some improvements to how users experience Detectify. In this update, we’ve split the configuration section, where our users can set up Detectify for the best coverage possible, and the insights section, where our users get continuous information about their ever changing attack surface.

We hope these changes to the navigation menu help users find the information they’re looking for quicker so they can get the most out of their attack surface insights.
Attack Surface:
Users will now be able to access all of their assets, technologies, and root assets directly from a dropdown in the menu, making it easier to find what you are looking for.
Vulnerabilities:
Users will now be able to access “open”, “fixed”, “accepted risked”, and “false positive” by selecting the drop down arrow.
Wondering which domains host specific technologies?
As we mentioned earlier, users can now see which technologies are hosting on their attack surface. In this update, we’ve now made it possible for users to view which technologies are hosted for specific domains.
Recently added crowdsourced vulnerabilities
Here is a list of all new medium, high, and critical severity modules added in the recent days from our community of ethical hackers. You can find a complete list of new vulnerabilities added to Surface Monitoring and Application Scanning by viewing the “What’s New?” section in-tool.
- AWStats Hostinfo XSS
- CodeIgniter Installer Exposure
- Discourse Installer Exposure
- NodeBB Web Installer Exposure
- NGINX Plus misconfigured content cache purge
- OpenShift Assisted Installer Exposure
- PHP Server Monitor Installer Exposure
- Softaculous Webuzo Installer Exposure
- Symfony PrestaImageBundle Arbitrary File Read
- UniFi Wizard Installer Exposure
- CVE-2022-0342: Zyxel CGI Authentication Bypass
- CVE-2022-0735: GitLab CE/EE – Runner Registration Token Disclosure
- CVE-2022-1281: WordPress Plugin “Photo Gallery by 10Web – Mobile-Friendly
- CVE-2022-1442: WordPress Plugin Metform Information Disclosure
- CVE-2022-31814: pfSense pfBlockerNG Plugin Remote Command Execution
- CVE-2022-35653: Moodle LTI module Reflected XSS
- CVE-2022-40881: Solarview RCE
Log in to get an overview of what is exposed on your attack surface.
Join our team
We’re hiring engineers, product managers, sales, & more! Learn more.







