AppSec teams often struggle to either validate or scale their security policies, like enforcing security headers or removing risky technologies. This job is easier said than done, and teams are feeling the pinch.
To address these challenges, we launched Attack Surface Custom Policies – a powerful feature built directly into Surface Monitoring that makes it possible to set, enforce, and scale customizable security policies so you can focus on the issues that matter most.
Recently, we launched a new capability to Attack Surface Custom Policies that allows you to set custom policies on technologies across your attack surface. With this update, you can assign a severity rating to a custom policy.
Why would I use severity ratings with Attack Surface Custom Policies?
Your vulnerability management system is likely using a rating system, often following the INFORMATION, LOW, MEDIUM, HIGH, and CRITICAL model. This means that you probably have a set of actions to be taken if a vulnerability receives a certain severity rating which helps your team prioritize the threat. By introducing severity ratings to policies, you can ensure these breaches are remediated according to your existing workflows.
We will publish more information on recommendations for severity based on your unique risk context in a later update.
Setting rules on fingerprinted technologies now possible
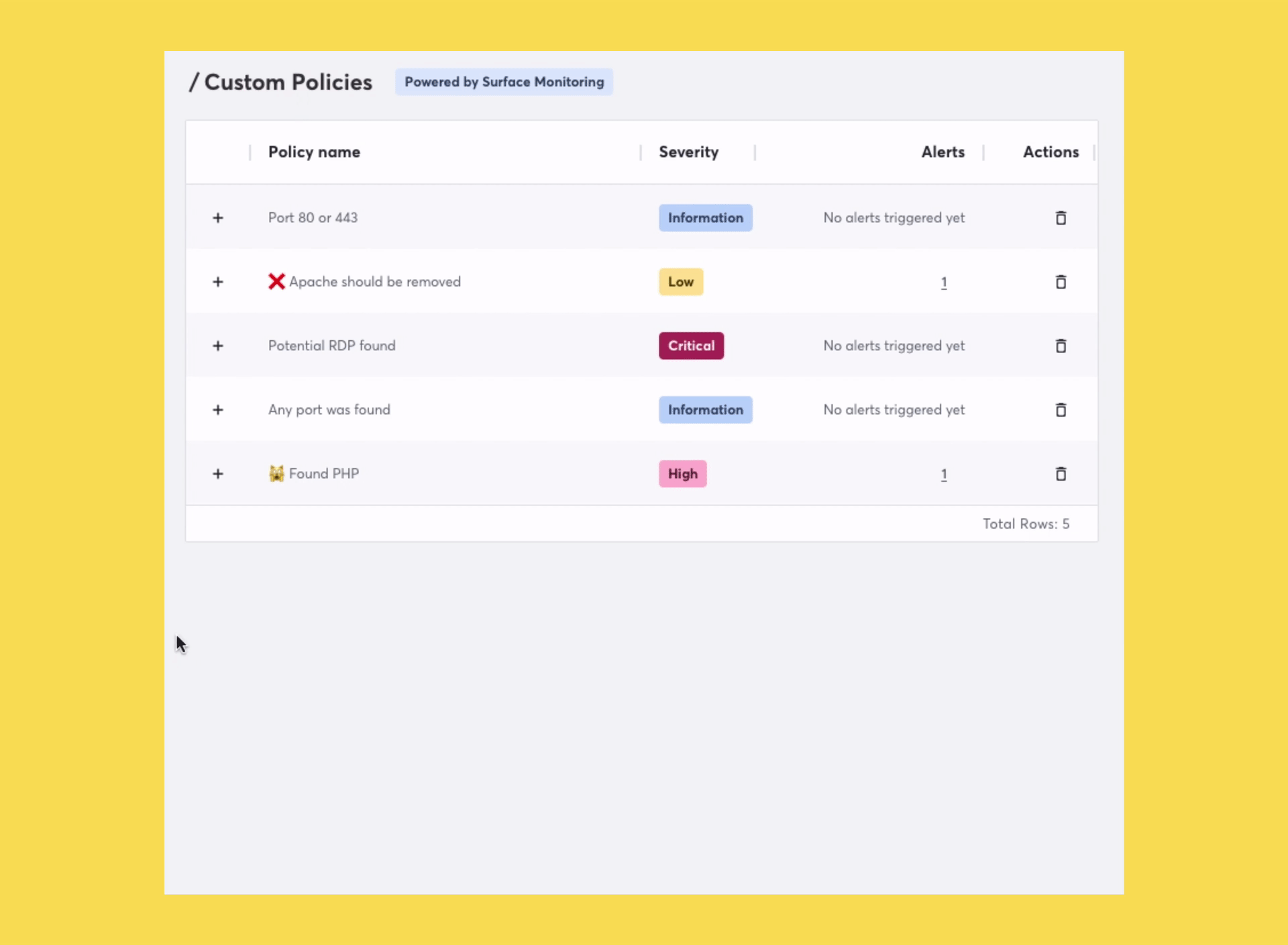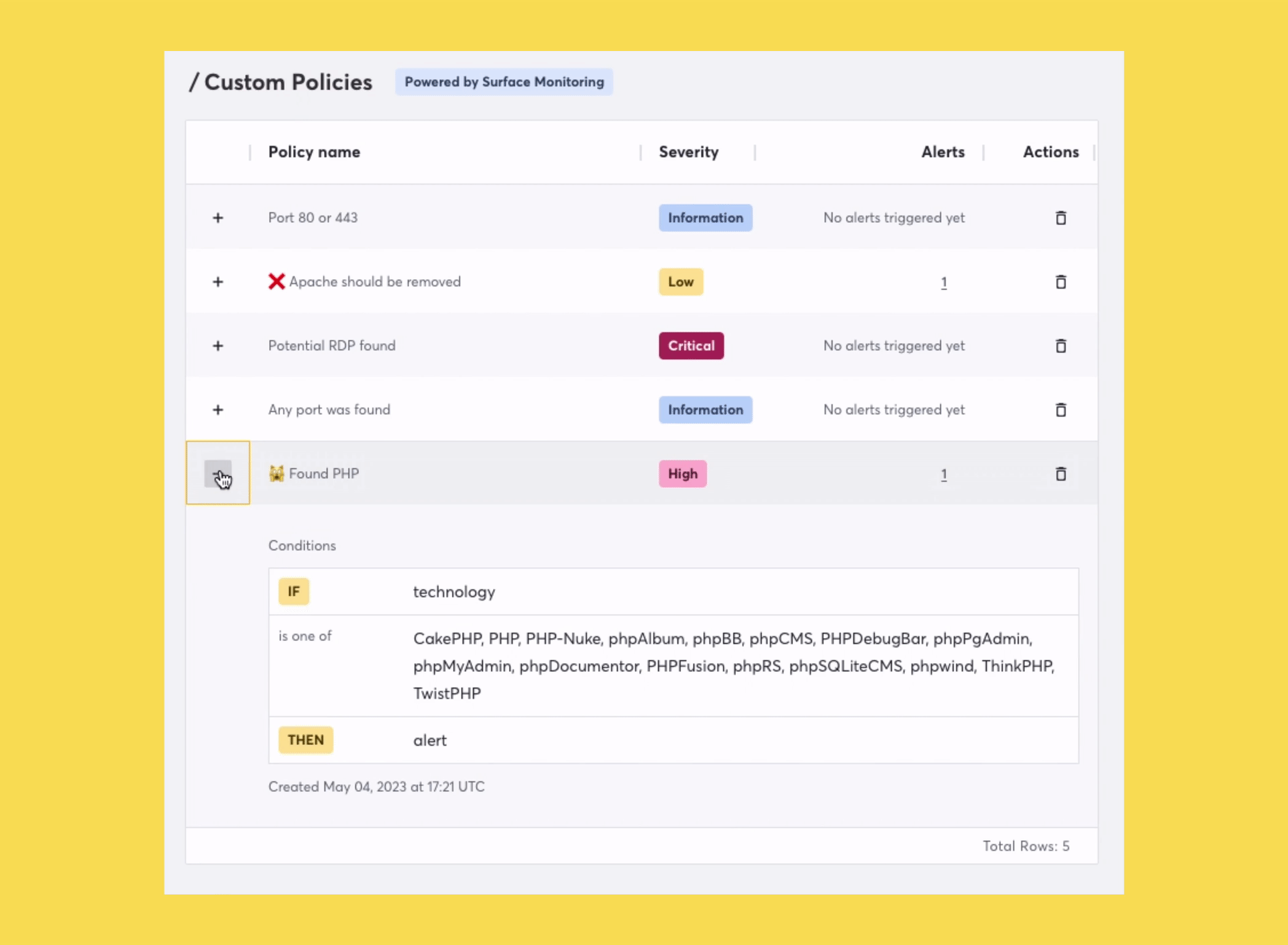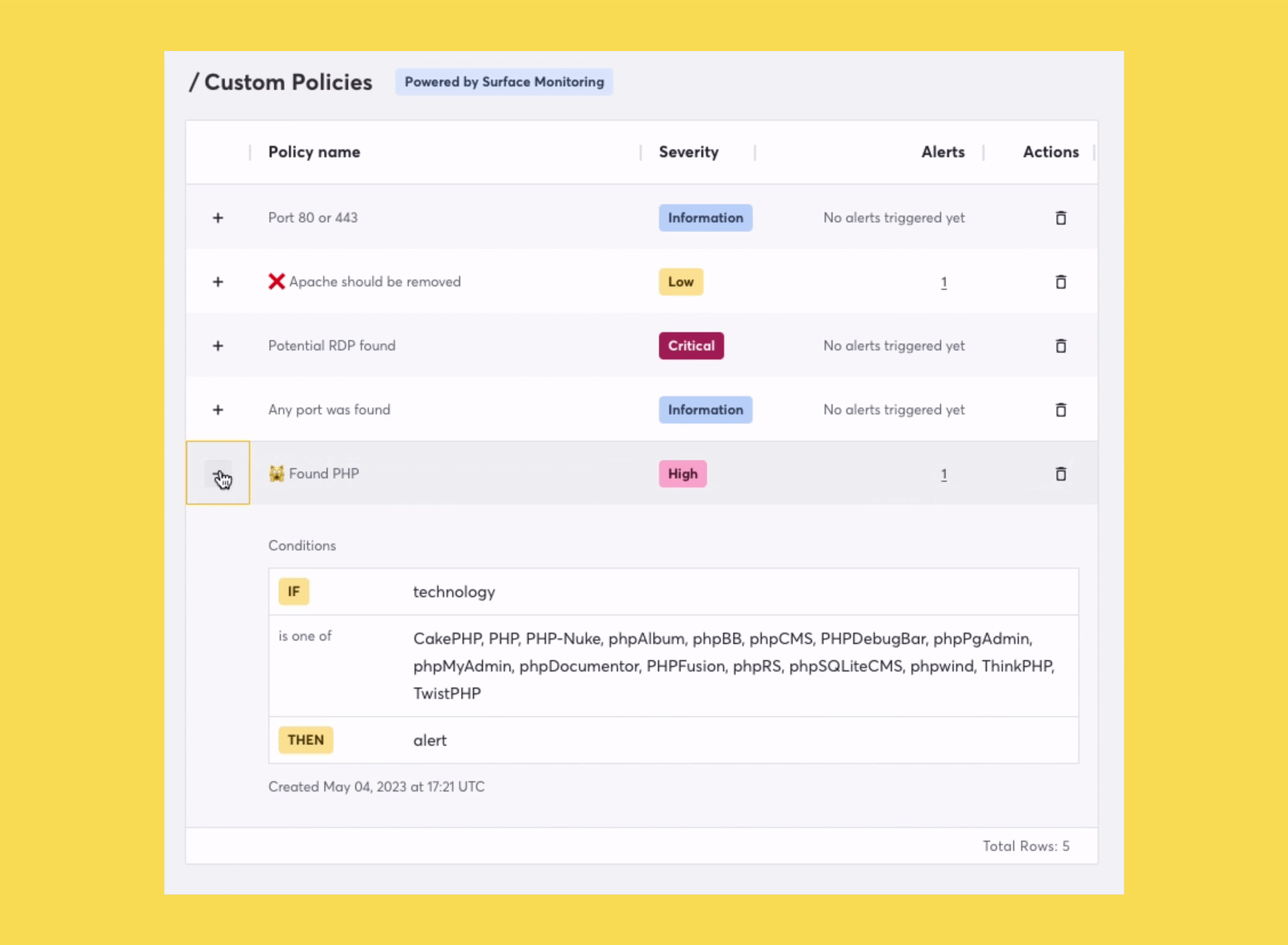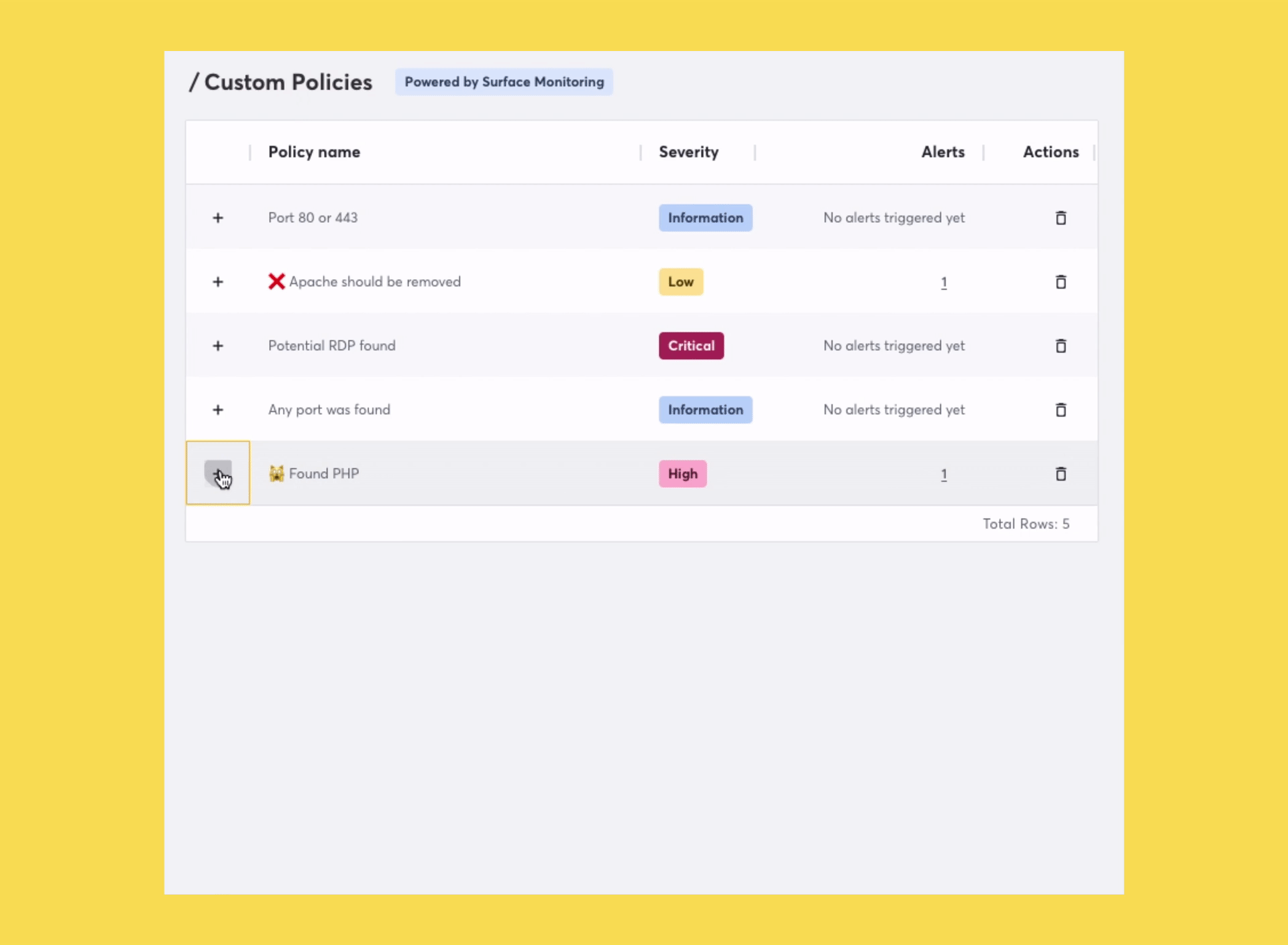
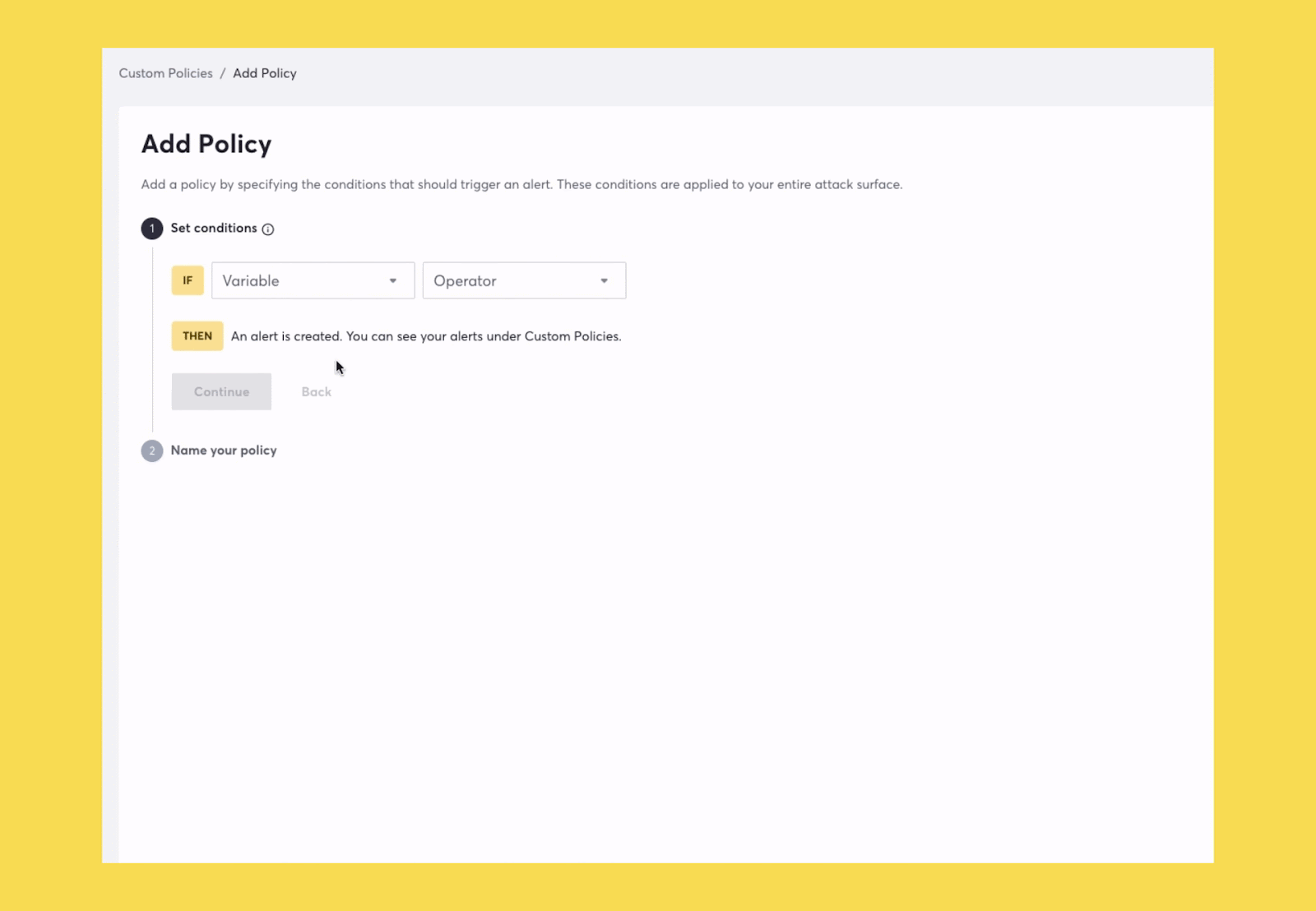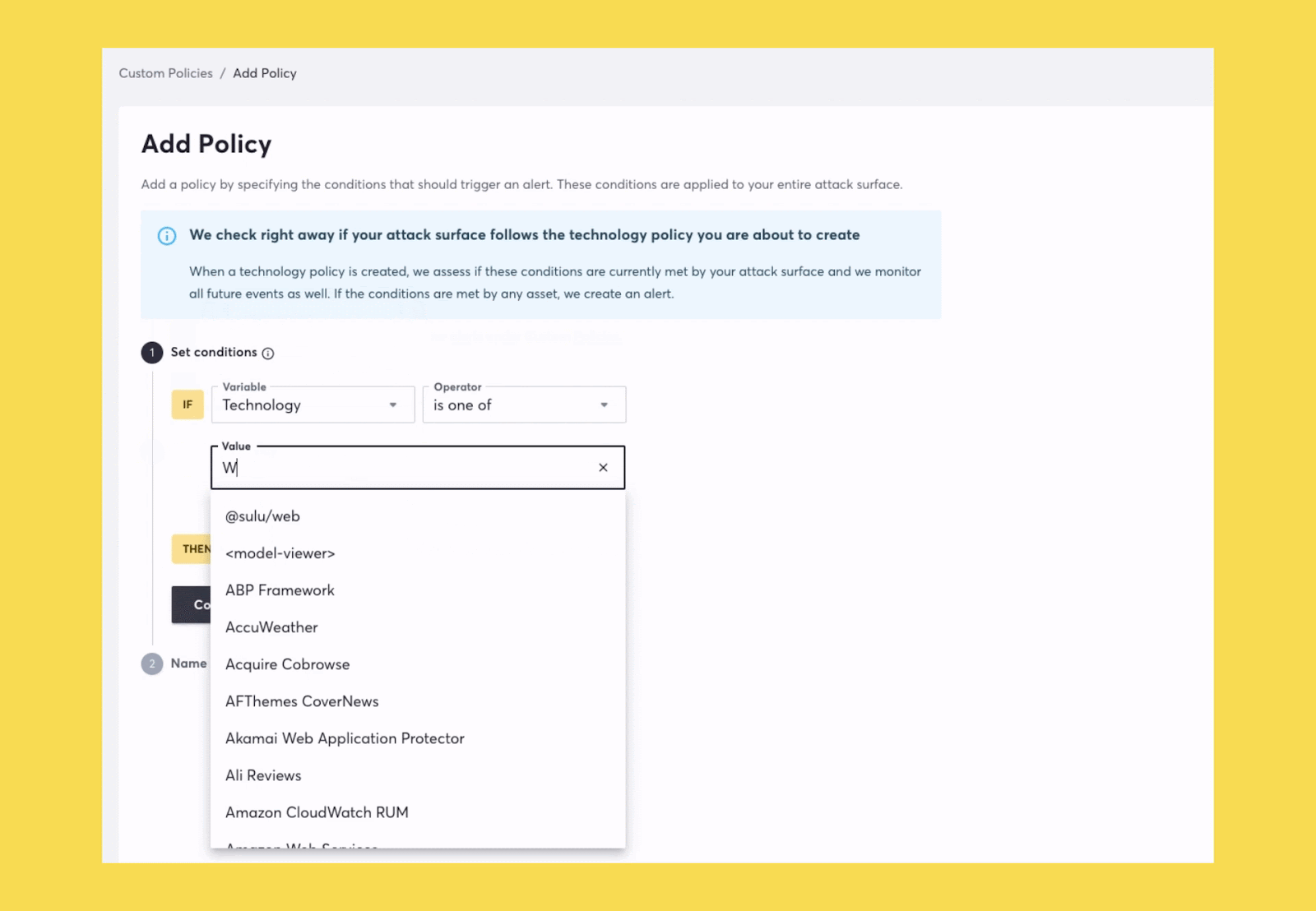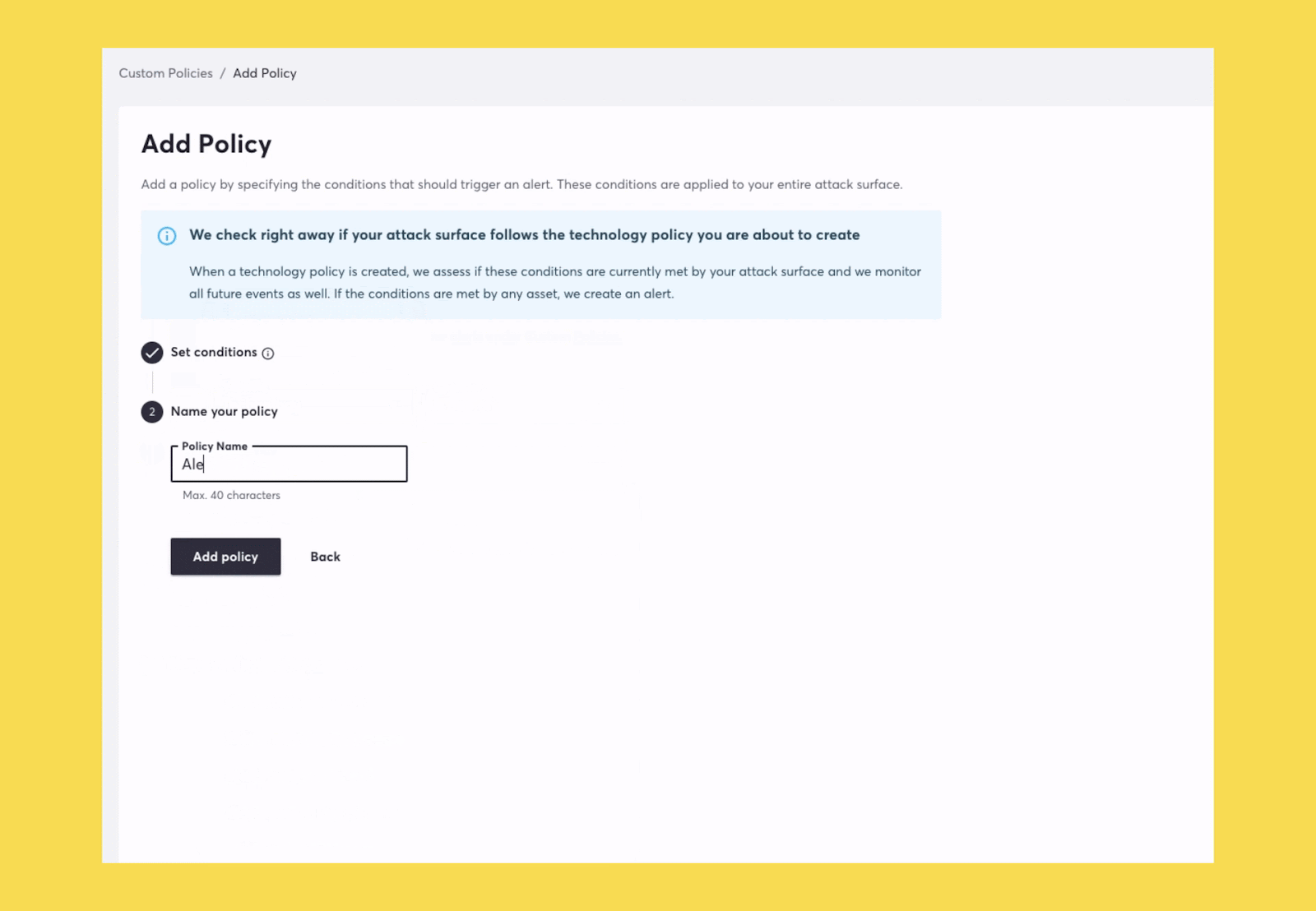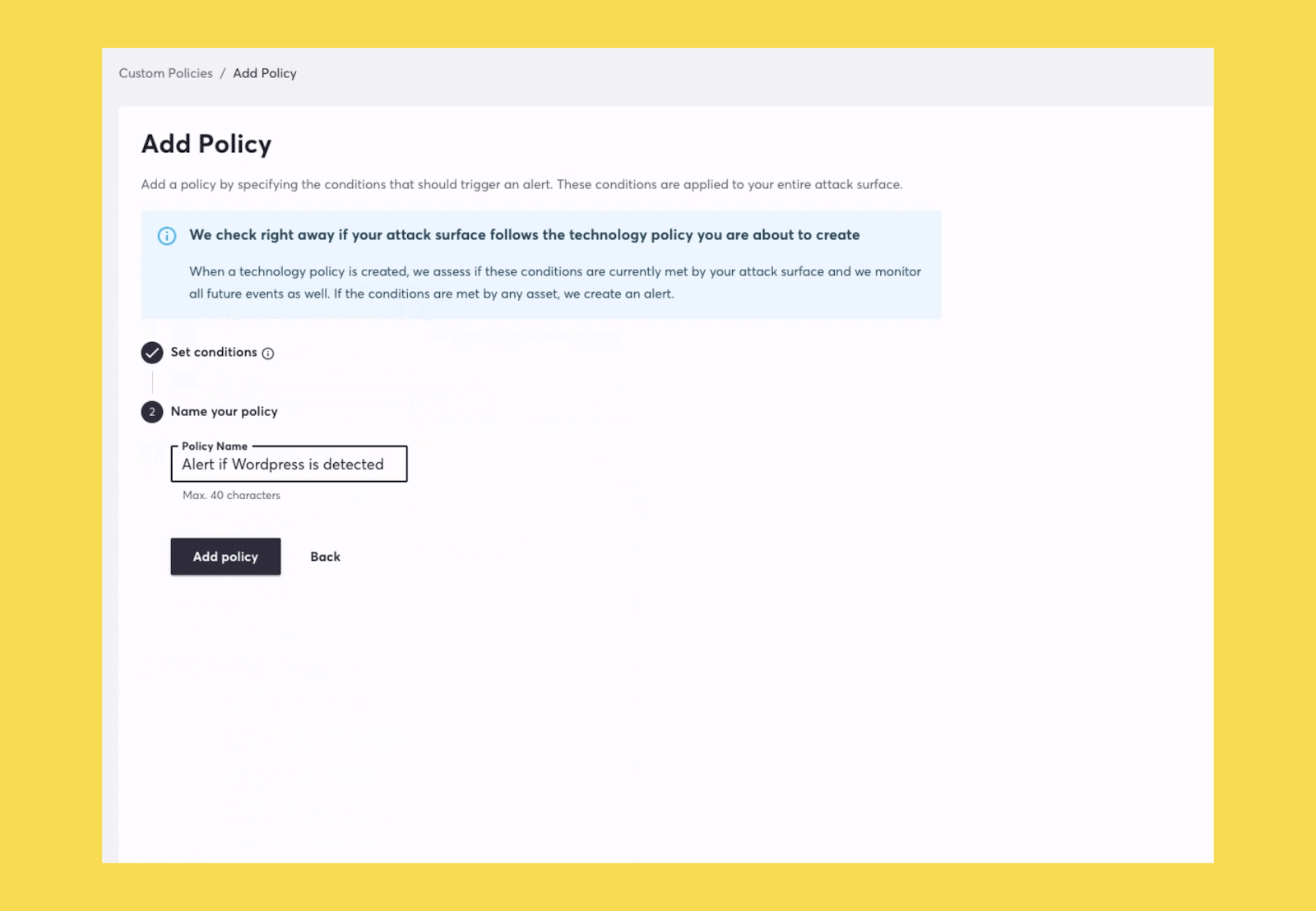
We’ve made several improvements since launching Attack Surface Custom Policies earlier this year. As mentioned above, one of these improvements now makes it possible to spot risks due to technologies discovered across your attack surface. This new functionality will help security teams with several jobs they need to get done.
“As part of our modernization efforts, I need to find all instances of a particular technology to deprecate.”
Whether you are going through a modernization process or just consolidating your tech, Attack Surface Custom Policies will now be able to accelerate that process by automating the discovery of technologies that you no longer want used in your organization. You can read about other use cases here.
Additional product updates:
- Technologies on the attack surface are now grouped by versions under the same row which we hope will simplify how you interact with your attack surface.
- The Attack Surface and Vulnerabilities page now function similarly, such as how you apply filters.
Already using Detectify?
Log in to get an overview of what is exposed on your attack surface. If you’re not using Detectify, consider trying it out by signing up today.







