All Surface Monitoring users can configure Attack Surface Policies directly from the new Domains page, enabling various combinations of characteristics that were previously unavailable. Users are now alerted when policy breaches occur directly through their integrated tools, such as Slack and Jira.
Making attack surface data actionable
Our users are responsible for the security of their digital products and services. We know it’s important for them to have the latest attack surface data enabling them to investigate exposures, set security policies, and respond quickly to vulnerabilities. We launched our new domains page to help our users get this job done.
Users can now filter several characteristics about their attack surface at a glance. A user might ask, “Do I have any instances where I am hosting data with AWS in countries that aren’t allowed?” This user can now filter their domains page to answer this question in Detectify, something that would have otherwise required them to get in touch with their teammates responsible for their cloud services.

But that only solves half the equation. Compliance requirements also inform internal security policies, such as limiting the use of cloud providers like AWS or GPC in specific geographies. Users can now set security policies directly from their domains page as they work with their attack surface data.
Detecting over 300 breaches per policy
We have observed over 300 breaches per policy created. Users may also set their own severity for each policy that reflects their organization’s risk tolerance. This underscores the need for a flexible and sustainable workflow for policy breaches. Accessing policy breaches via our API and integration offers both the flexibility and scalability that our users need long-term for prioritization and remediation.
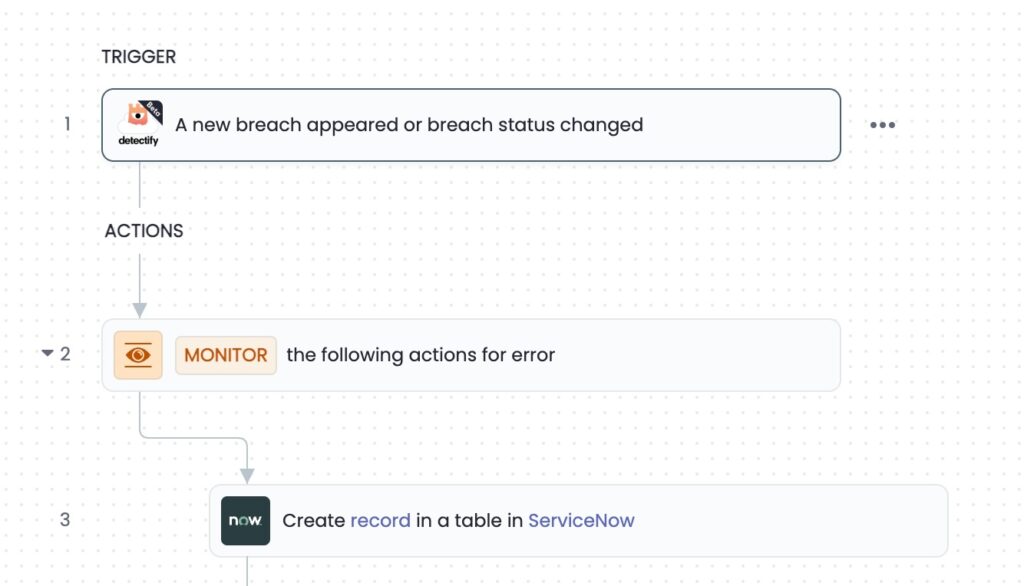
Get alerted for new policy breaches with integrations
Previously, users were required to log into Detectify to work with policy breaches, which doesn’t suit the needs of our medium to large sized customers. Now, users can integrate policy breaches into their preferred workflow using our integration platform and our public API. You can also fully customize your automation of policy breaches using the public API.
Our top 3 policies we think you should create
Creating and enforcing security policies is a challenge for our users tasked with securing the attack surface, usually with leaner teams and fewer resources. Security Policies addresses this challenge by embedding it in Detectify. Some challenges, however, are more common than others. Here are our top three policies that can help you get started:
- Alert me if there are specific service providers used in non-approved countries. Many organizations are operating in more than one geography, which comes with challenges around data security. We recommend users set up policies on their cloud service providers for specific geographies to help spot those breaches when they occur.
- Alert me if any port that is not 80 or 443 becomes open. Over 70% of active security policies today are configured to spot potentially risky open ports, such as ports associated with database traffic.
- Alert me if a specific technology is detected on these assets. Organizations usually have development guidelines, such as prohibited technologies with known vulnerabilities. Users can set up policies to spot prohibited tech or anything that is not permitted.
Security Policies are only available to Surface Monitoring customers. If you’re interested in trying this feature out, reach out to us via your CSM or support@detectify.com.







