
Product comparison: Detectify vs. Acunetix
Detectify vs Acunetix is a common comparison for AppSec teams evaluating Dynamic Application Security Testing (DAST) tools. This article provides a direct comparison between Detectify …

“How does Detectify compare to Penetration testing” or “What I’m really looking for is Penetration testing” are two statements that we often hear when talking to prospects. We know that many of you are keen to understand how automated tools and Penetration testing (Pen testing) compare, so we’re exploring these two methodologies side-by-side.
Application security testing and Penetration Testing (Pen Testing) enhance an organization’s cybersecurity posture but differ in scope, objectives, and capabilities.
When using Detectify’s AST solution, you can immediately start scanning your cloud environments to immediately identify misconfigurations and vulnerabilities. Detectify provides AppSec teams with a comprehensive overview of their organization’s current security state, helping them understand which assets are exposed to the Internet.
By discovering both known and, importantly, unknown assets, security teams can quickly address vulnerabilities and issues, ensuring that their organization adheres to internal security policies.
Ultimately, Detectify offers teams the ability to move quickly on the threats that affect their organization most.
Performed by skilled security experts who try to compromise a web application, in-depth Penetration Testing (Pen Testing) helps discover vulnerabilities and identify complex attack vectors through simulated cyber-attacks.
Pen Testing usually occurs within a particular scope and with specific permissions, with pen testers attempting to breach a system’s security using the same tools as a malicious actor. It is often (but not always) driven by an organization’s compliance needs.
Most organizations leverage Pen Testing only a few times a year, resulting in prioritizing remediation of vulnerabilities discovered several weeks or even months ago.
Each methodology will provide security teams with insights into vulnerabilities, anomalies, and risks that malicious actors could potentially exploit, but variations between Detectify and Pen Testing appear in the following capabilities:
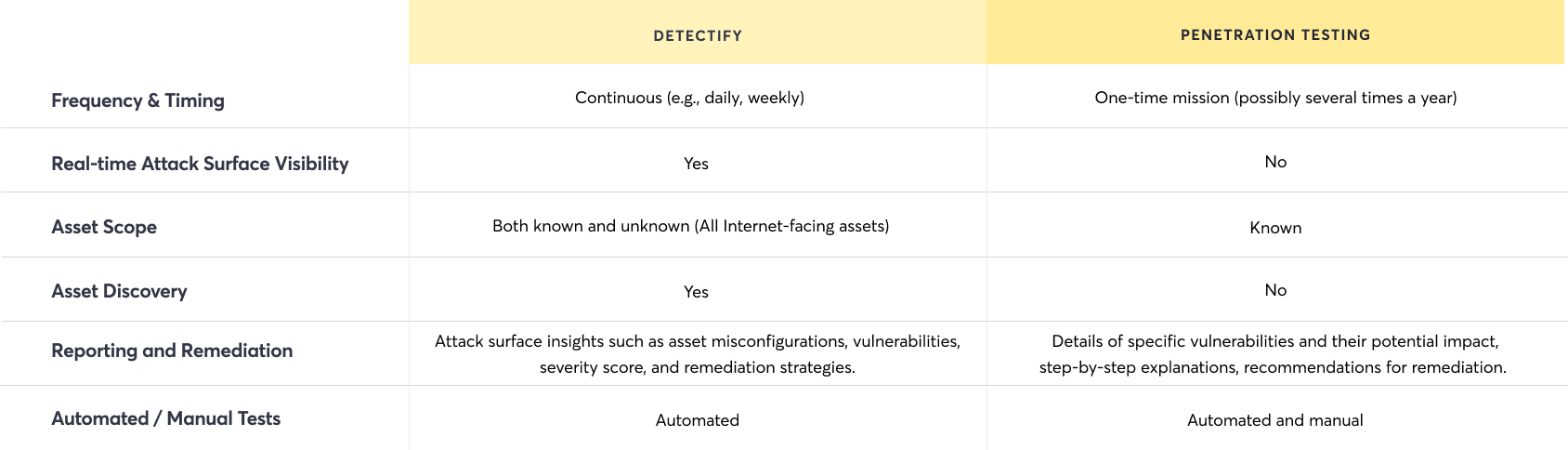
Table overview of how these capabilities compare
The more eyeballs (methodologies) thrown at an application, the more will be discovered. However, many traditional approaches to Application Security are built on the assumption that an organization is already aware of its Internet footprint and defines its scope for testing from the beginning.
Even though Pen Testing is a critical tool within many security toolkits, one of its major downsides is its inability to keep up with the rate of change of a modern attack surface and modern applications.
While most organizations opting for Pen Testing do it annually, today’s modern technology stacks also require constant monitoring.
While most organizations opting for Pen Testing do it annually, today’s modern technology stacks require constant monitoring. Applications are usually updated weekly, if not daily, resulting in reports that quickly become outdated and, at best, reflect only an organization’s security posture at a particular point in time.
For this reason, automated tools and Pen Testing can -and ideally should- be complementary. Automated tools can provide organizations with a broad understanding of their external risks and help them plan and prioritize Pen Tests to validate the effectiveness of security controls. The aim of using automated tools like Detectify is to challenge pen testers further, ensuring they work with an already well-hardened application.
Are you interested in learning more about Detectify? Start a 2-week free trial or talk to our experts.
If you are a Detectify customer already, don’t miss the What’s New page for the latest product updates, improvements, and new security tests.

Detectify vs Acunetix is a common comparison for AppSec teams evaluating Dynamic Application Security Testing (DAST) tools. This article provides a direct comparison between Detectify …

Applications have long evolved from monolithic structures to complex, cloud-native architectures. This means that the tried-and-true methods we rely on are becoming dangerously outdated. For …