
Introducing Protocol Discovery to stop guessing what’s behind your open ports
Most tools will just tell you that a port is open. We’ve decided that’s not enough. TLDR: We’ve launched Protocol Discovery, a custom-built engine designed …

Victor Arellano

The attack surface is where you can understand what you have exposed and whether you should take action on it. Previously, users couldn’t see which assets were vulnerable from the Attack Surface view – it was only possible to view vulnerable assets from the Vulnerabilities page, which required more time.
Viewing vulnerabilities on the Attack Surface page will help you better prioritize which assets you need to take action on. Each solution enables a different user flow; either you start from a prioritized list of vulnerabilities or start from the view of your attack surface. Both options are important in different ways.
Users can still access all of their vulnerabilities from the Vulnerabilities page in the tool. For example, you might notice that an asset on the Attack Surface view has a particular vulnerability type that could majorly impact your systems. In this scenario, you can go to the Vulnerability page to look for similar vulnerability types by using the pages’ broad query and filtering options.
We know that one of the jobs you need to get done is getting an overview of what is vulnerable so you can quickly take action. Our new Overview makes it possible for you to see a variety of risk factors, such as vulnerabilities by severity, assets with the most vulnerabilities, and the latest breaches of security policies.
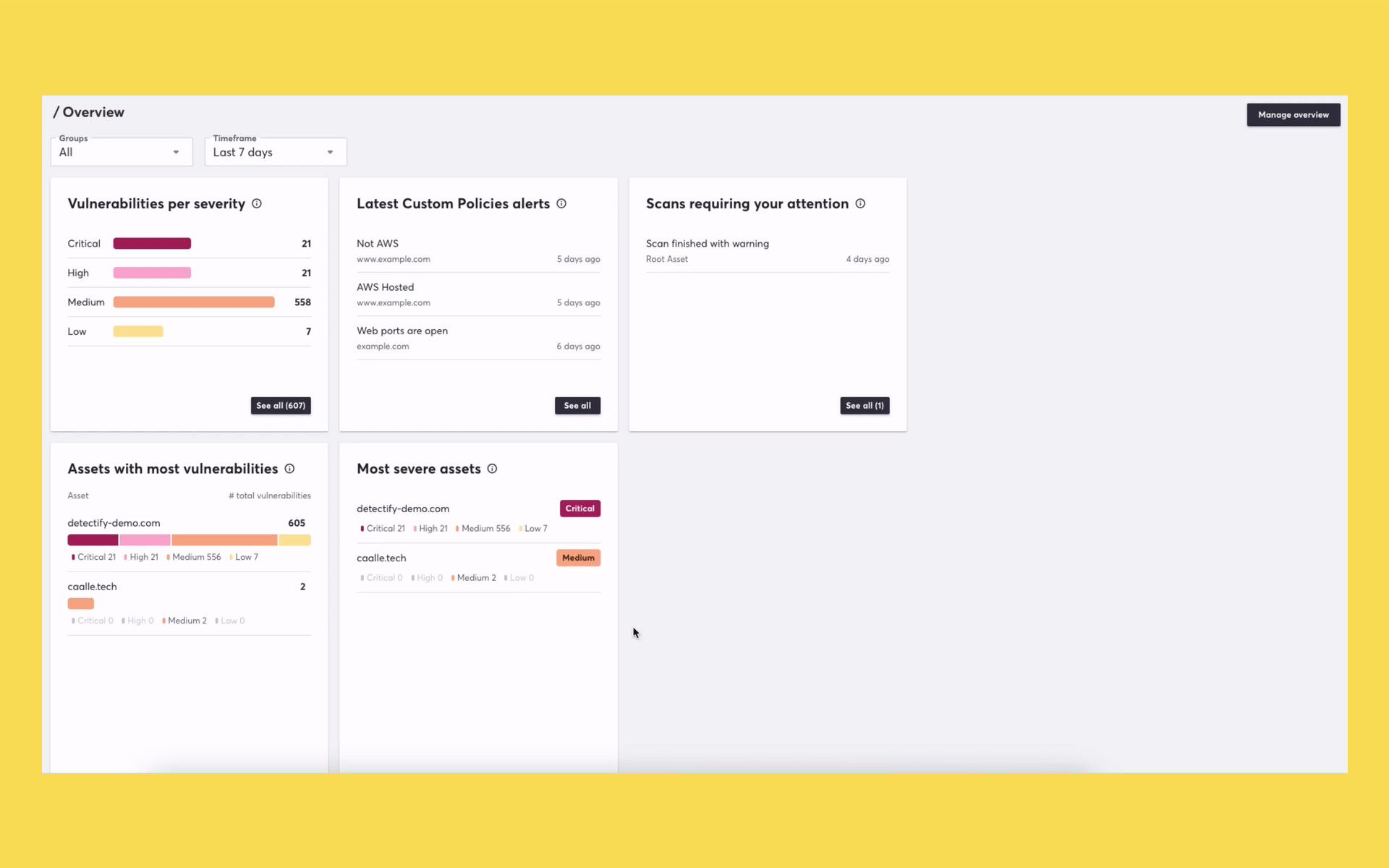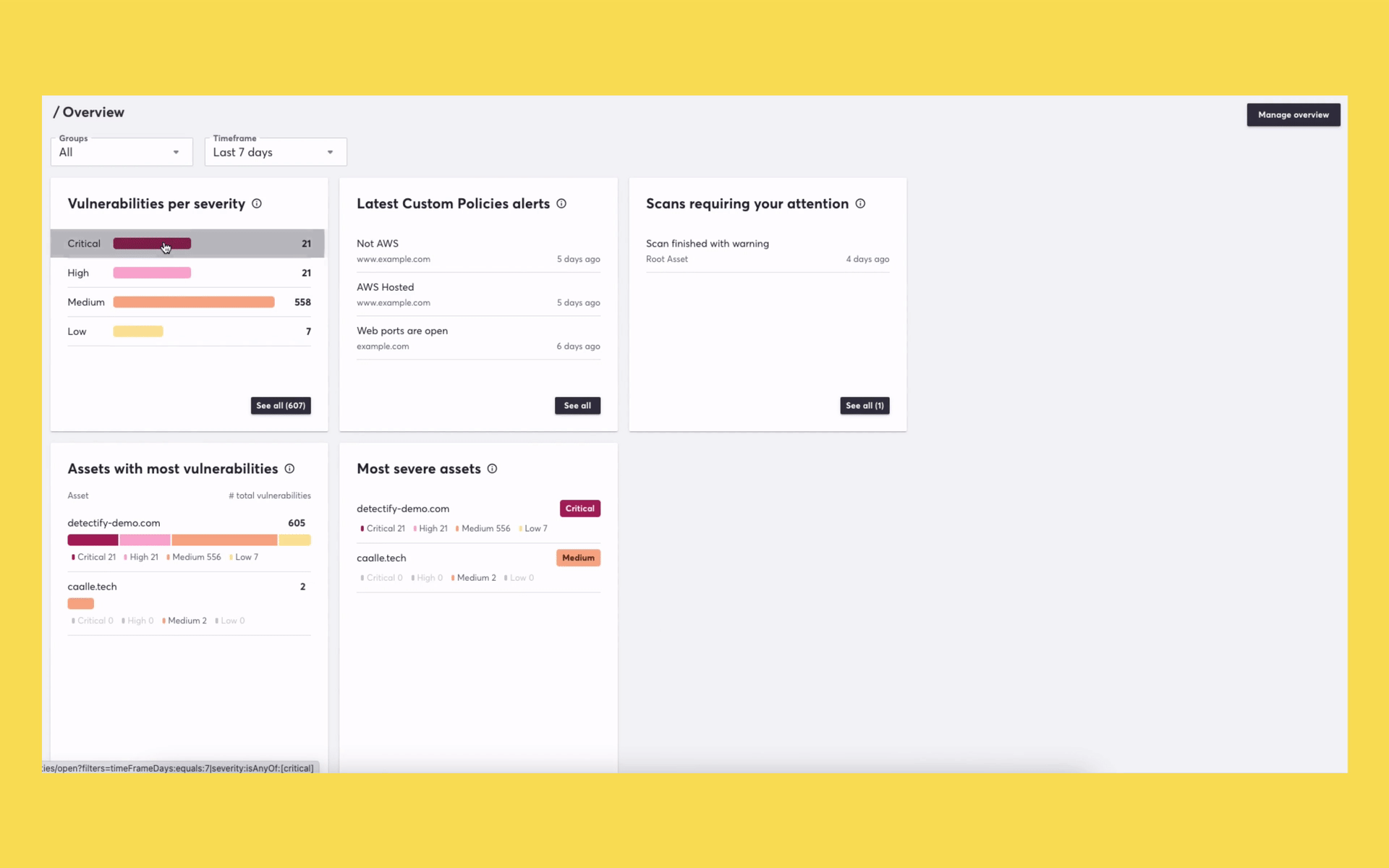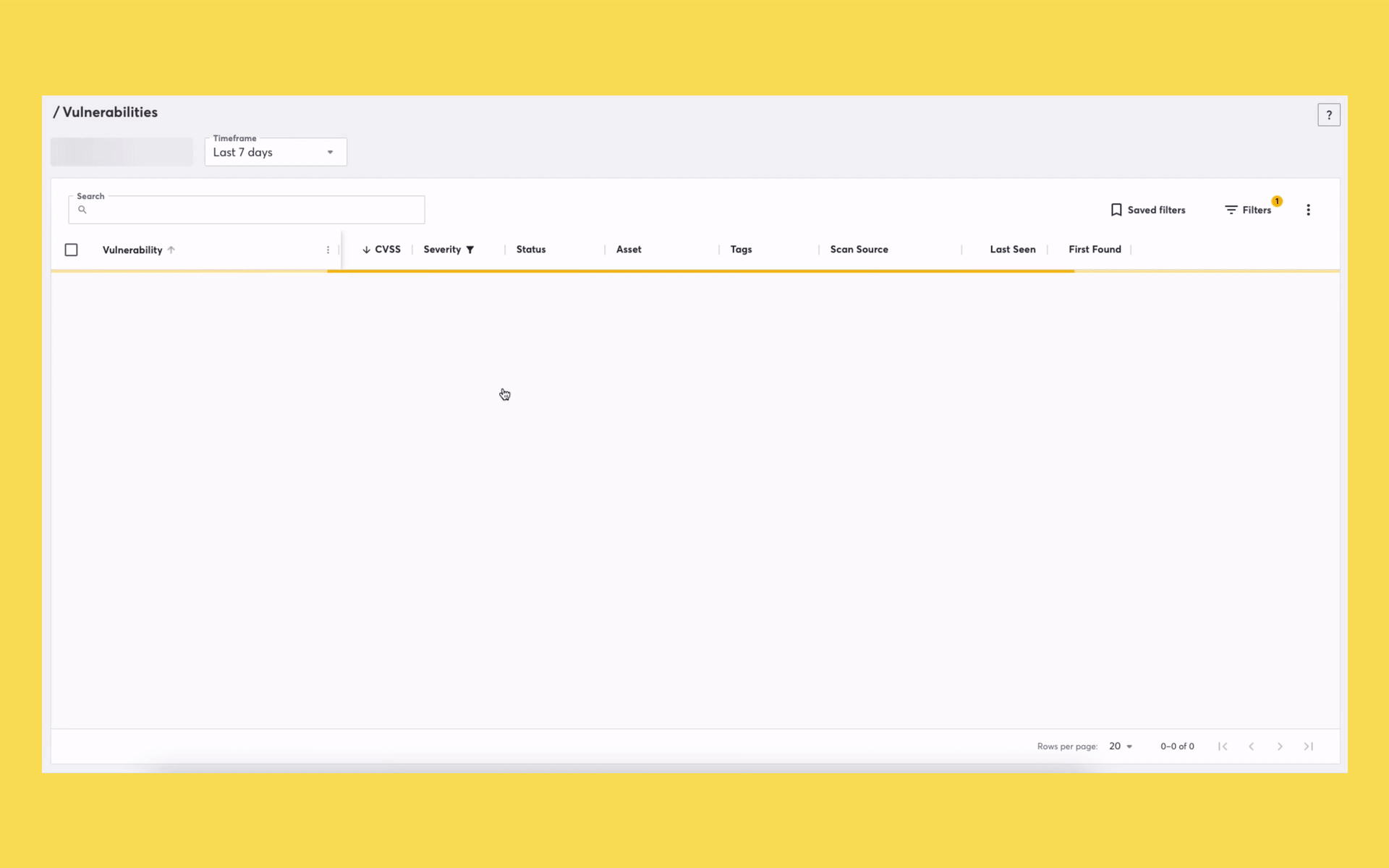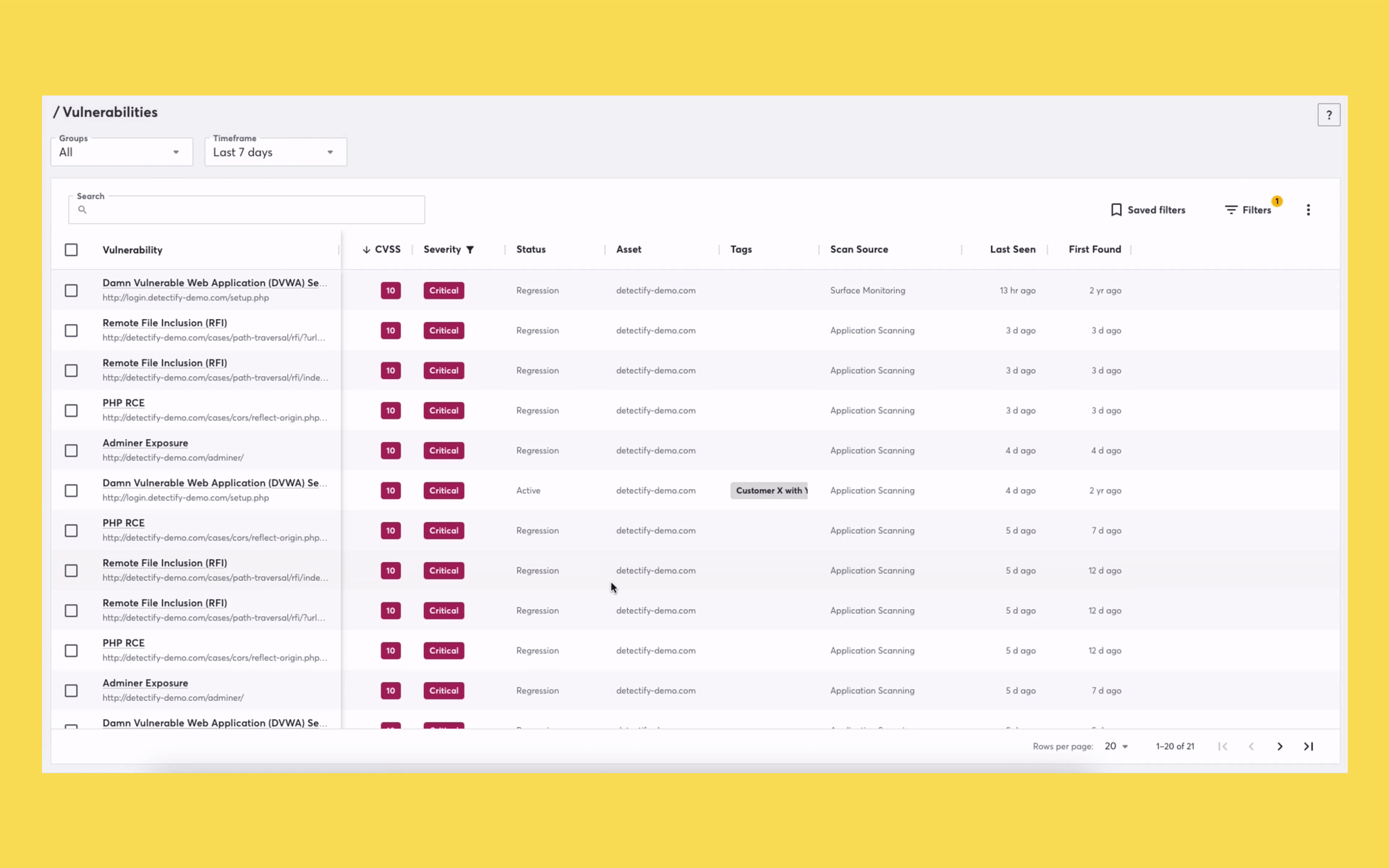
The previous dashboard will no longer be available. Want to check out the new Overview but not a customer yet? We demoed the new Overview during our last product release webinar. Check out our Knowledge Base article if you’d like to learn more about the new Overview.
Attack Surface Custom Policies have enabled users to set, enforce, and scale customizable security policies. In our most recent update to this feature, users can now add a specific cluster of domains when setting up their policies. For example, you might have a list of technologies that aren’t allowed on certain assets. Previously, any created policies were enforced across your entire attack surface, and any breach would trigger an alert. Now, you can specify more specific policies that only trigger for the parts of your attack surface where they are supposed to apply.
By specifying domains that are supposed to be protected by a VPN (and thus not supposed to expose open ports), you can ensure that your VPN is not misconfigured and accidentally exposing internal domains externally.
Here is a list of all new modules recently added from our community of ethical hackers. You can find a complete list of new vulnerabilities added to our platform by viewing the “What’s New?” section in-tool.
Already using Detectify? Log in to get an overview of what is exposed on your attack surface. If you’re not using Detectify, consider trying it out by signing up today for a free 2-week trial.

Most tools will just tell you that a port is open. We’ve decided that’s not enough. TLDR: We’ve launched Protocol Discovery, a custom-built engine designed …

TL;DR We’re launching Internal Scanning, bringing our proprietary security engines, research-led crawling and fuzzing engine for internal vulnerability scanning behind your firewall. Built by Detectify’s …