A lot could go wrong on the internet! A clever attacker can with ease gather all the intelligence he/she needs in order to conduct a full fledged exploit to reveal all the usernames (emails) and passwords of your website.
1. An attacker finds your website.

2. The attacker pinpoints if an SQL injection flaw is present.

3. The attacker resolves relevant data regarding the vulnerability.
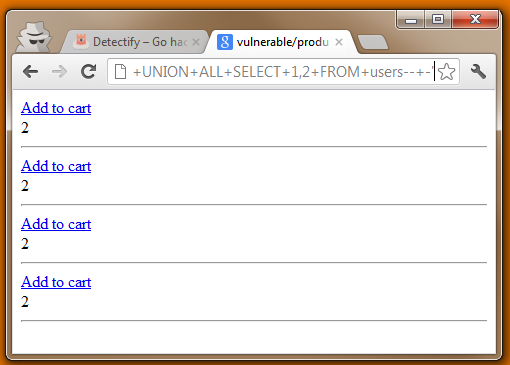
4. The attacker forges an exploit and steals your confidential information
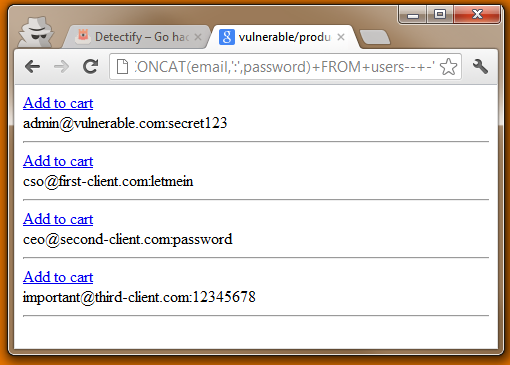
If an attacker found a hole like this when you started reading, chances are that he/she already has your database by now. That’s how easy it can be from an attackers point of view.If you got any questions, please send us an email at info@detectify.com.








